HMAC-SHA256 Accelerator
The all-RTL solution provides a fast and secure way to calculate a SHA256 hash for any message of any length. When combined with a secret key, it can also construct a HMAC keyed-hash message authentication code, which can be used to protect messages that are sent, and verify those that are received. The HMAC-SHA256 accelerator accepts multiple independent streaming messages/channels and support any number of arbitrary length messages. Number of channels is limited only by the memory resources provided, embedded Block RAM or external DDR. Typical use cases include highly secure RTL solutions where a CPU is unable to meet the required throughput and security performance.
View HMAC-SHA256 Accelerator full description to...
- see the entire HMAC-SHA256 Accelerator datasheet
- get in contact with HMAC-SHA256 Accelerator Supplier
Block Diagram of the HMAC-SHA256 Accelerator IP Core
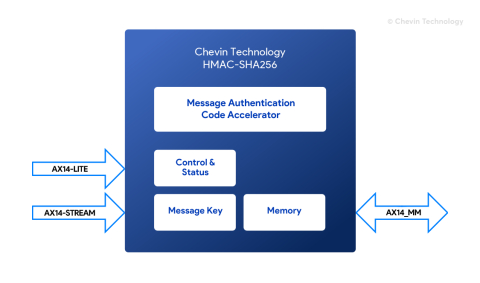
HMAC-SHA256 Accelerator IP
- Whirlpool Crypto Accelerator
- AES-ECB-CBC-CFB-CTR-GCM 1 Billion Trace DPA & Fault Injection Resistant Crypto Accelerator
- Secure-IC's Securyzr™ Tunable Public Key Cryptographic (RSA, ECDSA, SM2, Diffie-Hellman) accelerator - optional SCA protection
- Secure-IC's Securyzr™ Tunable Hash (SHA1-SHA2) Hardware accelerator
- Secure-IC's Securyzr™ Tunable AES (ECB, CBC, CTR, XTS, CCM, GCM) accelerator - optional SCA protection
- Secure-IC's Securyzr™ High-performance AES-GCM accelerator - optional SCA protection








