PUF-based Secure Crypto Coprocessor
The security boundary for PUFcc is quite robust, based on physical separation of hardware, with less vulnerability than a software-only barrier. The on-board PUF is a naturally well-protected source of static entropy, suitable for SoC architects to build a system’s key hierarchy using established key generation and management procedures. In addition, PUFcc’s crypto engines can perform a wide variety of secure operations, such as key exchange, secure boot or TLS (public key validation and signing), authentication (MAC), or key wrapping (again based on the natural randomness inherent to the PUF) and store said wrapped keys to external memory.
View PUF-based Secure Crypto Coprocessor full description to...
- see the entire PUF-based Secure Crypto Coprocessor datasheet
- get in contact with PUF-based Secure Crypto Coprocessor Supplier
Block Diagram of the PUF-based Secure Crypto Coprocessor IP Core
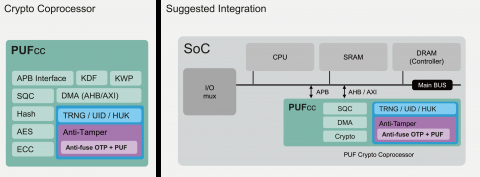
crypto coprocessor IP
- Secure-IC's Securyzr Crypto Coprocessor with integrated Post-Quantum Cryptography IPs
- Secure-IC's Securyzr(TM) Crypto Coprocessor (Standard)
- Secure-IC's Securyzr(TM) Crypto Coprocessor (Compact)
- Secure-IC's Securyzr(TM) Crypto Coprocessor (Premium)
- Upgraded PUF-based Crypto Coprocessor (Compliant with TLS 1.3 / FIPS 186-5)








