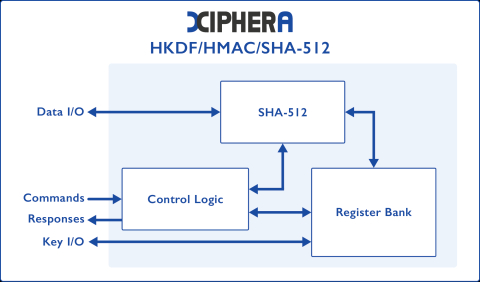
SHA-2 Hash Function (SHA-512) - Balanced variant
Xiphera's comprehensive hash function IP portfolio ensures the security and integrity of data through robust cryptographic standards. Supporting both SHA-2 and SHA-3 algorithm families, these solutions provide versatile functionality for various applications, from data integrity verification to password security. Our hash function portfolio is powered by Xiphera’s in-house designed IP cores, optimised for efficiency and high performance in FPGA and ASIC implementations.
View SHA-2 Hash Function (SHA-512) - Balanced variant full description to...
- see the entire SHA-2 Hash Function (SHA-512) - Balanced variant datasheet
- get in contact with SHA-2 Hash Function (SHA-512) - Balanced variant Supplier
Block Diagram of the SHA-2 Hash Function (SHA-512) - Balanced variant