I. Stamoulis, P. Kolokytha, T. Roudas and G. Sidiropoulos, Think Silicon Ltd
Patras, Greece
Abstract :
We present an on-line tool for the generation of Configurable IP modules that can be used in Semiconductor devices. This tool allows the generation of customized IP modules, configured according to user requirements which are packaged and delivered to the end-user via the Internet. In this paper we illustrate the operation of IPGenius platform, an on-line engine developed with special attention to security and data protection that is critical in the semiconductor IP industry.
INTRODUCTION
Gartner defines1 semiconductor intellectual property (IP) as predesigned blocks of circuits for use in making complete semiconductor devices. Traditionally Semiconductor IP blocks are designed by teams of engineers as blocks that are individually integrated into system-on-chip and custom semiconductor devices. The need to shorten design time and the evolutionary nature of many devices demands the use of design-reuse methodologies. In a design reuse methodology, semiconductor IP modules are designed to be easily reused in future products with little or no modifications.
To further improve reusability of modules, these have to be very generic and able be to used in many different scenarios of applications. Their parameters must be customizable, to allow the user to select features needed, and omit other features that are not necessary for a particular implementation and their inclusion would only add complexity affecting area and power consumption.
GENERIC DESIGN
High level hardware description languages like VHDL and Verilog provide methods to create generic implementations. However, in many cases either it is not possible to describe all possible combinations using generic constructs or it imposes a higher complexity circuit to the synthesis process.
The idea of on-line generation of circuit descriptions is not new; there are several individual examples available on the network that generate modules like CRC equations and arithmetic operators2.
However, our tool is a configurable and expandable platform that can be used as a framework for the development of a complete on-line IP portfolio.
WEB FRONT-END GENERATOR
To further simplify the selection, parameterization and generation of IP modules, we propose a Graphical User Interface available through a web front end and on-line generation of the IP source code.
The initial step in the usage of the system is the registration of a user. In the user management menu, registered users can enter their details, their public GPG key for receiving encrypted data and browse the generation history, i.e, a review of modules requested with their parameters.
The next step consists of browsing the available on-line IP modules. The user can view the datasheet, the revision history and the license of each module.
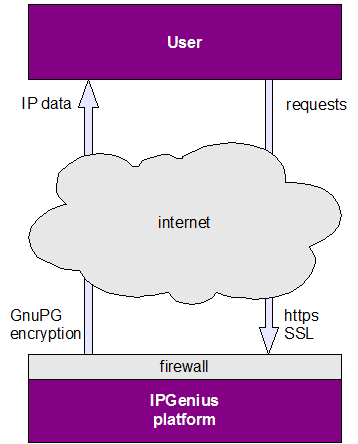
Illustration 1: Web front and Security
Once an IP module is selected, the configuration parameters can be set. The generator is invoked with the specified parameters and the requested components are generated. Documentation, Synthesis scripts and all other supporting material is packaged into a single archive, which is delivered to the user via email.
SECURITY AND DATA PROTECTION
Security and Data Protection is the most important challenge in the design of an on-line IP generation and delivery platform. As we regard all data exchanged via the Internet to be subject to interception at any time, mechanisms to ensure data protection and integrity, have the highest priority Protection of Intellectual Property is of utmost importance to both IP Receiver and IP Provider. However, as Internet security technologies have matured and secure methods for data exchange are reliable, we believe with very high confidence that data can be protected against interception, corruption and manipulation. We employ the following technologies to ensure data security:
We believe that the integration of the two methods mentioned above with standard unix security for protecting the public webserver, can provide a very high level of security for IP data, important both for IP Receivers and IP Providers.
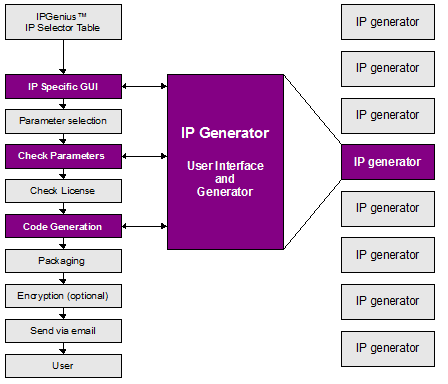
Illustration 2: IPGenius Flow and API with model Generator
IPGENIUS FLOW
The diagram on the illustration 2 depicts how IPGenius operates internally and the steps taken from the user GUI to the IP delivery:
The user enters the Think Silicon IPGenius Environment via a standard web browser. He can select a module from an increasing selection of IP modules. Each IP Module has a bespoke parameter selection window, documentation information, revision history changes and licensing scheme. The tool holds a database with all the available IP modules and their GUI front end, the parameters, revision history and licensing information.
Upon submission, the tool checks for licensing requirements and user eligibility for the particular module. The tool holds a database of licenses and users. If the user holds a valid license for the particular module the tool proceeds to the next steps of the generator. If the business model is to request a fee on a checkout basis, we ensure at this stage enough credits available are to obtain the module.
After the License requirements are verified, then the input parameters are checked for sanity. Many fields will allow for arbitrary values to be entered, but at this stage we will verify what is reasonable for the particular module.
The next step is the invocation of the IP Generator script. The user-defined parameters are passed to a scripting language that prepares the source code according the user requirements. We have selected the perl language as the basis of our tool as it is portable and very powerful in manipulating text files like source code. The generator writes all generated source HDL files, and other supporting files like custom documentation and XML-metadata. IP Cores with XML metadata as defined by the Spirit Consortium will allow smoother integration by ESL Design software.
The generated IP is packaged with additional general support files, such as documentation, related software, testbenches and synthesis scripts and is compressed to a single tar.gz file.
An optional GPG encryption step is inserted for modules that require encryption or if encryption for all modules is requested by the user. In this step, the file is encrypted using the public GPG key from the user profile. The user must first enter his public key in the relevant section of profile settings and validate it. This will ensure that the receiving party can only use the file and even if it is intercepted on the Internet by any means, it will not provide useful data to the interceptor.
The final IP is emailed as an attachment to the user and is available in his mailbox. Even for complicated design the entire process only takes a few seconds and the user can receive the requested module in the exact requested specification immediately.
EXAMPLE
The following pictures show how IPGenius can be used to generate a customized AMBAâ„¢ AHB interconnection fabric with user defined number of masters, slaves and decoding address table.
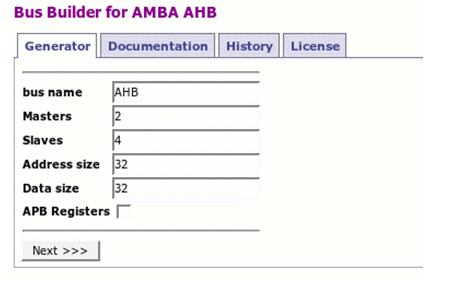
Illustration 3: General parameter entry
Initially the user is presented with a menu with a selection of parametrizable modules. Each module has a unique configuration window that allows the user to select parameters. There are additional tabs, with information about the module, including documentation, revision history and license agreement.
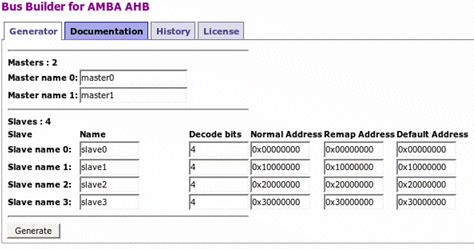
Illustration 4: Custom parameter entry
The User selects the AHB Bus Builder module, he is presented with a menu asking for some basic parameters to be generated. In this particular case the design is customizable in terms of the number of masters, the number of slaves and the width of the address/data buses. It is also possible to define the name of the generated module, a useful feature, as many different instantiations may exist in the same design.
After the basic parameters are defined, the user is presented with a second customized menu that prompts for further parameters based on the previously selected options. In this particular case, the user can select the names of the masters and slaves, a useful feature for easily identifying the relation between signals and interconnected modules. For the Slaves, the user can enter the name of each of the slaves and an address decoding table for all modes of operation.
The user can then select the generation of the selected module. The IPGenius engine will generate all the HDL code, the documentation, the tool scripts for synthesis and XML metadata for use by ESL tools. It will then proceed by packaging it into a single archive, encrypting it if so required by the license requirements, and finally delivering it to the user via email.
ALTERNATIVE OPERATION MODELS
The use of an on-line tool to generate customized modules can also form the basis for alternative business models that are not currently available in the industry. The platform can support three types of modules:
We believe that the IPGenius tool and the online delivery methodology will present a lot of benefits to VLSI IC Designers:
REFERENCES - ENDNOTES
1) Gartner, Inc. (http://www.gartner.com/it/page.jsp?id=495502)
2) Most Notable examples are eASICS CRC generator and Arithmetic Module from Tohoku University, Japan.
Patras, Greece
Abstract :
We present an on-line tool for the generation of Configurable IP modules that can be used in Semiconductor devices. This tool allows the generation of customized IP modules, configured according to user requirements which are packaged and delivered to the end-user via the Internet. In this paper we illustrate the operation of IPGenius platform, an on-line engine developed with special attention to security and data protection that is critical in the semiconductor IP industry.
INTRODUCTION
Gartner defines1 semiconductor intellectual property (IP) as predesigned blocks of circuits for use in making complete semiconductor devices. Traditionally Semiconductor IP blocks are designed by teams of engineers as blocks that are individually integrated into system-on-chip and custom semiconductor devices. The need to shorten design time and the evolutionary nature of many devices demands the use of design-reuse methodologies. In a design reuse methodology, semiconductor IP modules are designed to be easily reused in future products with little or no modifications.
To further improve reusability of modules, these have to be very generic and able be to used in many different scenarios of applications. Their parameters must be customizable, to allow the user to select features needed, and omit other features that are not necessary for a particular implementation and their inclusion would only add complexity affecting area and power consumption.
GENERIC DESIGN
High level hardware description languages like VHDL and Verilog provide methods to create generic implementations. However, in many cases either it is not possible to describe all possible combinations using generic constructs or it imposes a higher complexity circuit to the synthesis process.
The idea of on-line generation of circuit descriptions is not new; there are several individual examples available on the network that generate modules like CRC equations and arithmetic operators2.
However, our tool is a configurable and expandable platform that can be used as a framework for the development of a complete on-line IP portfolio.
WEB FRONT-END GENERATOR
To further simplify the selection, parameterization and generation of IP modules, we propose a Graphical User Interface available through a web front end and on-line generation of the IP source code.
The initial step in the usage of the system is the registration of a user. In the user management menu, registered users can enter their details, their public GPG key for receiving encrypted data and browse the generation history, i.e, a review of modules requested with their parameters.
The next step consists of browsing the available on-line IP modules. The user can view the datasheet, the revision history and the license of each module.

Illustration 1: Web front and Security
Once an IP module is selected, the configuration parameters can be set. The generator is invoked with the specified parameters and the requested components are generated. Documentation, Synthesis scripts and all other supporting material is packaged into a single archive, which is delivered to the user via email.
SECURITY AND DATA PROTECTION
Security and Data Protection is the most important challenge in the design of an on-line IP generation and delivery platform. As we regard all data exchanged via the Internet to be subject to interception at any time, mechanisms to ensure data protection and integrity, have the highest priority Protection of Intellectual Property is of utmost importance to both IP Receiver and IP Provider. However, as Internet security technologies have matured and secure methods for data exchange are reliable, we believe with very high confidence that data can be protected against interception, corruption and manipulation. We employ the following technologies to ensure data security:
- SSL access: Access to the IPGenius program can take place via Secure Sockets Layer protected web pages. SSL and TLS are cryptographic protocols that provide secure communications and endpoint authentication and communications over the Internet using proven cryptographic techniques. Typically, only the server is authenticated (i.e., its identity is ensured) while the client remains unauthenticated; this means that the end user (whether an individual or an application, such as a Web browser) can be sure with whom they are communicating. SSL access will guarantee that communications from the users browsers to our server remains confidential and it will not be possible to intercept data entered in forms, or parameters enter when requesting modules.
- GPG Delivery: We used the opensource GNU Privacy Guard (available from GnuPG http://www.gnupg.org) private-public key encryption mechanism to encrypt the data sent. GnuPG allows encrypting and signing your data and communication. Signing of data is important for the user to trust that received data originates from our server and is not modified enroute, either by malicious hackers, or by data corruption. The process we employ to utilize encryption, is to allow the user to enter his public GPG key in his user profile. The key is then validated on our server and a validation code is sent in encrypted form via email. The user can enter this validation key in his profile and enable encryption.
We believe that the integration of the two methods mentioned above with standard unix security for protecting the public webserver, can provide a very high level of security for IP data, important both for IP Receivers and IP Providers.

Illustration 2: IPGenius Flow and API with model Generator
IPGENIUS FLOW
The diagram on the illustration 2 depicts how IPGenius operates internally and the steps taken from the user GUI to the IP delivery:
The user enters the Think Silicon IPGenius Environment via a standard web browser. He can select a module from an increasing selection of IP modules. Each IP Module has a bespoke parameter selection window, documentation information, revision history changes and licensing scheme. The tool holds a database with all the available IP modules and their GUI front end, the parameters, revision history and licensing information.
Upon submission, the tool checks for licensing requirements and user eligibility for the particular module. The tool holds a database of licenses and users. If the user holds a valid license for the particular module the tool proceeds to the next steps of the generator. If the business model is to request a fee on a checkout basis, we ensure at this stage enough credits available are to obtain the module.
After the License requirements are verified, then the input parameters are checked for sanity. Many fields will allow for arbitrary values to be entered, but at this stage we will verify what is reasonable for the particular module.
The next step is the invocation of the IP Generator script. The user-defined parameters are passed to a scripting language that prepares the source code according the user requirements. We have selected the perl language as the basis of our tool as it is portable and very powerful in manipulating text files like source code. The generator writes all generated source HDL files, and other supporting files like custom documentation and XML-metadata. IP Cores with XML metadata as defined by the Spirit Consortium will allow smoother integration by ESL Design software.
The generated IP is packaged with additional general support files, such as documentation, related software, testbenches and synthesis scripts and is compressed to a single tar.gz file.
An optional GPG encryption step is inserted for modules that require encryption or if encryption for all modules is requested by the user. In this step, the file is encrypted using the public GPG key from the user profile. The user must first enter his public key in the relevant section of profile settings and validate it. This will ensure that the receiving party can only use the file and even if it is intercepted on the Internet by any means, it will not provide useful data to the interceptor.
The final IP is emailed as an attachment to the user and is available in his mailbox. Even for complicated design the entire process only takes a few seconds and the user can receive the requested module in the exact requested specification immediately.
EXAMPLE
The following pictures show how IPGenius can be used to generate a customized AMBAâ„¢ AHB interconnection fabric with user defined number of masters, slaves and decoding address table.

Illustration 3: General parameter entry
Initially the user is presented with a menu with a selection of parametrizable modules. Each module has a unique configuration window that allows the user to select parameters. There are additional tabs, with information about the module, including documentation, revision history and license agreement.

Illustration 4: Custom parameter entry
The User selects the AHB Bus Builder module, he is presented with a menu asking for some basic parameters to be generated. In this particular case the design is customizable in terms of the number of masters, the number of slaves and the width of the address/data buses. It is also possible to define the name of the generated module, a useful feature, as many different instantiations may exist in the same design.
After the basic parameters are defined, the user is presented with a second customized menu that prompts for further parameters based on the previously selected options. In this particular case, the user can select the names of the masters and slaves, a useful feature for easily identifying the relation between signals and interconnected modules. For the Slaves, the user can enter the name of each of the slaves and an address decoding table for all modes of operation.
The user can then select the generation of the selected module. The IPGenius engine will generate all the HDL code, the documentation, the tool scripts for synthesis and XML metadata for use by ESL tools. It will then proceed by packaging it into a single archive, encrypting it if so required by the license requirements, and finally delivering it to the user via email.
ALTERNATIVE OPERATION MODELS
The use of an on-line tool to generate customized modules can also form the basis for alternative business models that are not currently available in the industry. The platform can support three types of modules:
- Time limited access to selected model. In this model of operation the user is granted unlimited usage of the generator platform within a predefined period of time.
- Checkout limited access to selected models. In this model, the user is granted a prespecified number of “checkouts†for a selected module.
- Free to use models, where users have unlimited access to obtain any desired configuration
We believe that the IPGenius tool and the online delivery methodology will present a lot of benefits to VLSI IC Designers:
- Users can immediately access a number of IP circuits without waiting for custom design by the IP provider.
- The designer will spend less time modifying modules to meet needs. Even simple generic modules often require significant engineering time to be customized to requirements.
- Our methodology will also allow for potential alternative business models that are currently not available in the Semiconductor industry. For example, it can be possible to allow access to a module for a lower initial fee and then charge on a checkout basis.
REFERENCES - ENDNOTES
1) Gartner, Inc. (http://www.gartner.com/it/page.jsp?id=495502)
2) Most Notable examples are eASICS CRC generator and Arithmetic Module from Tohoku University, Japan.
