"And one (key) to rule them all…"
As fevered blockchain talk starts to cool and quantum computing peeks over the far horizon, we are still living in a world where the internet of things (IoT) encompasses billions of connected devices (and growing every day!), each of which needs to be secured against breaches and attacks. But what is most important when protecting these IoT devices? It is Kerckhoffs’ principle that states that a cryptographic system should be secure even if every part of it is public except the key. Hence, the most important part of an IoT device to protect is its cryptographic root key.
The Key is Key
However, an IoT device rarely only has a single key. This is because for a security system to secure a device throughout its device lifecycle, it needs multiple cryptographic keys at different times in the cycle and for multiple users and purposes:
- To identify the device
- For secure boot and protecting the boot flow
- To make sure the right/legitimate firmware is loaded onto the device
- Application-related keys
- User keys
- To set up secure communication (e.g. authentication and session keys)
To further complicate the challenge, some of these keys are public and must be un-changeable, while others are private and must be kept secret. Some are long-lived (e.g., keys used to identify and authenticate the device), while others are only used once and for a short time (e.g., to set up a secure communication channel or encrypt a data package that needs to be send securely). Some keys are only available to the device itself, while others are used by the system, applications, or its users only. Some keys will be interacting with other connected devices in systems secured by varying cryptographic algorithms and that require keys with different lengths or different structures which are incompatible with each other.
For these and other reasons, it is a well-established best practice in security design to use a single key only for a single purpose and/or application. While security systems usually are based on a single root of trust (the cryptographic root key), in order to meet the single-key-single-use requirement, the solution must also include a key management component with the ability to generate multiple application keys from that single root secret.
These multiple derived application keys must be cryptographically separated: they should be generated in such a way that the disclosure of a derived key does not affect the security strength of any other derived key or the key it is derived from. A well-designed key derivation function uses state-of-the-art cryptographic primitives (e.g. AES or SHA-256) to ensure cryptographic separation between its outputs.
So, what’s required is a system that can create and protect a virtually unlimited number of strong, device-unique cryptographic keys of varying lengths and structures that can be used by multiple users throughout the supply chain. And all of the keys derived from the system must be cryptographically separated such that each key only serves one purpose and so that any one key being compromised will not compromise any other key.
Can one solution really meet all these needs? Intrinsic ID QuiddiKey can.
QuiddiKey: One Solution for a Lifetime of Security Needs
QuiddiKey was designed to meet the varied security needs – including key derivation and secure storage – of connected devices throughout their lifecycles.
The Root of Trust
The root of trust for QuiddiKey is the Intrinsic ID SRAM PUF technology, which has been deployed in more than 200 million devices worldwide. This technology, which takes advantage of random silicon process variations, has been proven reliable over the lifetime of devices and has been implemented technology nodes down to 7nm (and beyond). The root key that provides the single root secret for QuiddiKey is derived from the PUF response and is re-created each time a key is needed, so that the root key is never stored and is only a minimal amount of time present in the device, as it should be.
QuiddiKey for Secure Key Vaults
QuiddiKey utilizes the device-specific startup behavior of SRAM to create a unique root key for every chip. The QuiddiKey algorithms guarantee that this root key is different for every chip, while the same root key is reliably re-created on a specific device every time it is needed. By wrapping all additionally required keys with this root key (as shown in the chart below), these additional keys can be stored securely in any public non-volatile memory (NVM), either on or off chip. Because the root key is unique for every chip and is never stored, the confidentiality and integrity of all stored keys is ensured.
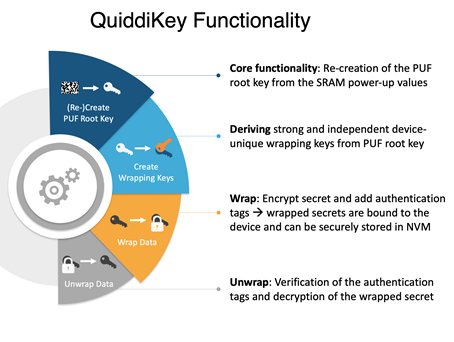
Compact, Flexible, Secure
QuiddiKey is implemented in a single, compact IP block, which makes it easy to include in designs. Despite this compactness, QuiddiKey can create and protect a virtually unlimited number of strong, device-unique, cryptographically separated keys (each key serves only one purpose). This means that even if the original designers didn’t foresee the need for a particular key by a particular user in the supply chain, QuiddiKey can create the needed key(s). QuiddiKey uses NIST-compliant/approved algorithms (AES, SHA-256, etc.) to ensure cryptographic separation.
QuiddiKey Driver Eases Integration
The QuiddiKey driver eases the use of the QuiddiKey hardware IP for developers in an embedded software environment. It is delivered as C source and comes with a reference manual, integration tests and the QuiddiKey register description. The operations in the chart above are also accessible in the QuiddiKey driver through the API functions.
Learn More
For more information on Intrinsic ID’s QuiddiKey IP, please visit: https://www.design-reuse.com/sip/secure-puf-ip-to-create-wrap-and-manage-keys-ip-36280/
